istio安装
istio官网安装提供了多种方法,因为集群中包含helm,所以选择用helm安装istio
- 下载istio release(目前版本为0.8.0)
- 命令行执行
helm install install/kubernetes/helm/istio --name istio --namespace istio-system(此命令采取自动注入sideCar)
istio的helm的value.yaml文件如下:# Use --set or additional values.yaml file to configure settings.
# This file no longer uses sed, updateVersions.sh or istio.VERSIONS
# TODO: evaluate if we need individual overrides for each component version, istio
# is not typically tested with a mix of versions. Only supported case is version upgrade.
# Common settings.
global:
# Default repository for Istio images.
# Releases are published to docker hub under 'istio' project.
# Daily builds from prow are on gcr.io, and nightly builds from circle on
# docker.io/istionightly
hub: 192.168.30.100:8889/istio
# Default tag for Istio images.
# Should track latest released version in the branch.
tag: 0.8.0
proxy:
image: proxyv2
resources:
requests:
cpu: 100m
memory: 128Mi
# istio-sidecar-injector configmap stores configuration for sidecar injection.
# This config map is used by istioctl kube-inject and the injector webhook.
enableCoreDump: false
serviceAccountName: default # used only if RBAC is not enabled
replicaCount: 1
resources:
requests:
cpu: 100m
memory: 128Mi
# limits:
# cpu: 100m
# memory: 128Mi
# istio egress capture whitelist
# https://istio.io/docs/tasks/traffic-management/egress.html#calling-external-services-directly
# example: includeIPRanges: "172.30.0.0/16,172.20.0.0/16"
# would only capture egress traffic on those two IP Ranges, all other outbound traffic would
# be allowed by the sidecar
includeIPRanges: "*"
excludeIPRanges: ""
# istio ingress capture whitelist
# examples:
# Redirect no inbound traffic to Envoy: --includeInboundPorts=""
# Redirect all inbound traffic to Envoy: --includeInboundPorts="*"
# Redirect only selected ports: --includeInboundPorts="80,8080"
includeInboundPorts: "*"
excludeInboundPorts: ""
policy: enabled
proxy_init:
image: proxy_init
# imagePullPolicy is applied to istio control plane components.
# local tests require IfNotPresent, to avoid uploading to dockerhub.
# TODO: Switch to Always as default, and override in the local tests.
imagePullPolicy: IfNotPresent
# Not recommended for user to configure this. Hyperkube image to use when creating custom resources
hyperkube:
repository: 192.168.30.100:8889/coreos/hyperkube
tag: v1.7.6_coreos.0
# controlPlaneMtls enabled. Will result in delays starting the pods while secrets are
# propagated, not recommended for tests.
controlPlaneSecurityEnabled: false
# Default mtls policy. If true, mtls between services will be enabled by default.
mtls:
# Default setting for service-to-service mtls. Can be set explicitly using
# destination rules or service annotations.
enabled: false
# List of fully qualified services to exclude from mtls
# TODO: add the templating.
mtlsExcludedServices:
- "kubernetes.default.svc.cluster.local"
# create RBAC resources. Must be set for any cluster configured with rbac.
rbacEnabled: true
## imagePullSecrets for all ServiceAccount. Must be set for any clustser configured with privte docker registry.
# imagePullSecrets:
# - name: "private-registry-key"
# Default is 1 second
refreshInterval: 10s
# Enable multicluster operation. Must be set to true if multicluster operation
# is desired.
multicluster:
enabled: false
# Specify pod scheduling arch(amd64, ppc64le, s390x) and weight as follows:
# 0 - Never scheduled
# 1 - Least preferred
# 2 - No preference
# 3 - Most preferred
arch:
amd64: 2
s390x: 2
ppc64le: 2
# Any customization for istio testing should be here
istiotesting:
oneNameSpace: false
#
# ingress configuration
#
ingress:
enabled: true
serviceAccountName: default
autoscaleMin: 1
autoscaleMax: 1
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
service:
loadBalancerIP: "10.100.100.20"
type: LoadBalancer #change to NodePort, ClusterIP or LoadBalancer if need be
ports:
- port: 80
name: http
nodePort: 32000
- port: 443
name: https
selector:
istio: ingress
#
# ingressgateway configuration
#
ingressgateway:
enabled: true
serviceAccountName: istio-ingressgateway-service-account
autoscaleMin: 1
autoscaleMax: 1
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
service:
name: istio-ingressgateway #DNS addressible
labels:
istio: ingressgateway
#namespace: istio-system
loadBalancerIP: "10.100.100.129"
type: LoadBalancer #change to NodePort, ClusterIP or LoadBalancer if need be
ports:
## You can add custom gateway ports
- port: 80
name: http
nodePort: 31380
- port: 443
name: https
nodePort: 31390
- port: 31400
name: tcp
nodePort: 31400
deployment:
labels:
istio: ingressgateway #will be added to pods and service
ports:
- containerPort: 80
- containerPort: 443
- containerPort: 31400
secretVolumes:
- name: ingressgateway-certs
secretName: istio-ingressgateway-certs
mountPath: /etc/istio/ingressgateway-certs
#
# egressgateway configuration
#
egressgateway:
enabled: true
serviceAccountName: istio-egressgateway-service-account
autoscaleMin: 1
autoscaleMax: 1
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
service:
name: istio-egressgateway #DNS addressible
labels:
istio: egressgateway
#namespace: istio-system
type: ClusterIP #change to NodePort or LoadBalancer if need be
ports:
## You can add custom gateway ports
- port: 80
name: http
- port: 443
name: https
deployment:
labels:
istio: egressgateway #will be added to pods and service
ports:
- containerPort: 80
- containerPort: 443
# secretVolumes: TODO
# - name: someName
# mountPath: somePath
# secretName: someName
#
# sidecar-injector webhook configuration
#
sidecarInjectorWebhook:
enabled: true
image: sidecar_injector
#
# galley configuration
#
galley:
enabled: false
serviceAccountName: default
replicaCount: 1
image: galley
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
#
# mixer configuration
#
mixer:
enabled: true
serviceAccountName: default # used only if RBAC is not enabled
replicaCount: 1
image: mixer
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
prometheusStatsdExporter:
repository: 192.168.30.100:8889/prom/statsd-exporter
tag: latest
resources: {}
#
# pilot configuration
#
pilot:
enabled: true
serviceAccountName: default # used only if RBAC is not enabled
replicaCount: 1
image: pilot
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
#
# security configuration
#
security:
enabled: true
serviceAccountName: default # used only if RBAC is not enabled
replicaCount: 1
image: citadel
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
cleanUpOldCA: true
#
# addons configuration
#
grafana:
enabled: true
replicaCount: 1
image: grafana
service:
name: http
type: ClusterIP
externalPort: 3000
internalPort: 3000
ingress:
enabled: false
# Used to create an Ingress record.
hosts:
- grafana.local
annotations:
# kubernetes.io/ingress.class: nginx
# kubernetes.io/tls-acme: "true"
tls:
# Secrets must be manually created in the namespace.
# - secretName: grafana-tls
# hosts:
# - grafana.local
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
prometheus:
enabled: true
replicaCount: 1
image:
repository: 192.168.30.100:8889/prom/prometheus
tag: latest
ingress:
enabled: false
# Used to create an Ingress record.
#hosts:
# - prometheus.local
annotations:
# kubernetes.io/ingress.class: nginx
# kubernetes.io/tls-acme: "true"
tls:
# Secrets must be manually created in the namespace.
# - secretName: prometheus-tls
# hosts:
# - prometheus.local
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
service:
nodePort:
enabled: false
port: 32090
servicegraph:
enabled: true
replicaCount: 1
image: servicegraph
service:
name: http
type: ClusterIP
externalPort: 8088
internalPort: 8088
ingress:
enabled: false
# Used to create an Ingress record.
hosts:
- servicegraph.local
annotations:
# kubernetes.io/ingress.class: nginx
# kubernetes.io/tls-acme: "true"
tls:
# Secrets must be manually created in the namespace.
# - secretName: servicegraph-tls
# hosts:
# - servicegraph.local
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
# prometheus addres
prometheusAddr: http://prometheus:9090
tracing:
enabled: true
jaeger:
enabled: true
memory:
max_traces: 50000
replicaCount: 1
image:
repository: 192.168.30.100:8889/jaegertracing/all-in-one
tag: 1.5
service:
name: http
type: ClusterIP
externalPort: 9411
internalPort: 9411
uiPort: 16686
ingress:
enabled: false
# Used to create an Ingress record.
hosts:
- zipkin.local
annotations:
# kubernetes.io/ingress.class: nginx
# kubernetes.io/tls-acme: "true"
tls:
# Secrets must be manually created in the namespace.
# - secretName: zipkin-tls
# hosts:
# - zipkin.local
resources: {}
# limits:
# cpu: 100m
# memory: 128Mi
# requests:
# cpu: 100m
# memory: 128Mi
主要修改了镜像地址和将以些默认不安装的addon设置为安装(grafana,servicegraph,tracing)
安装成功之后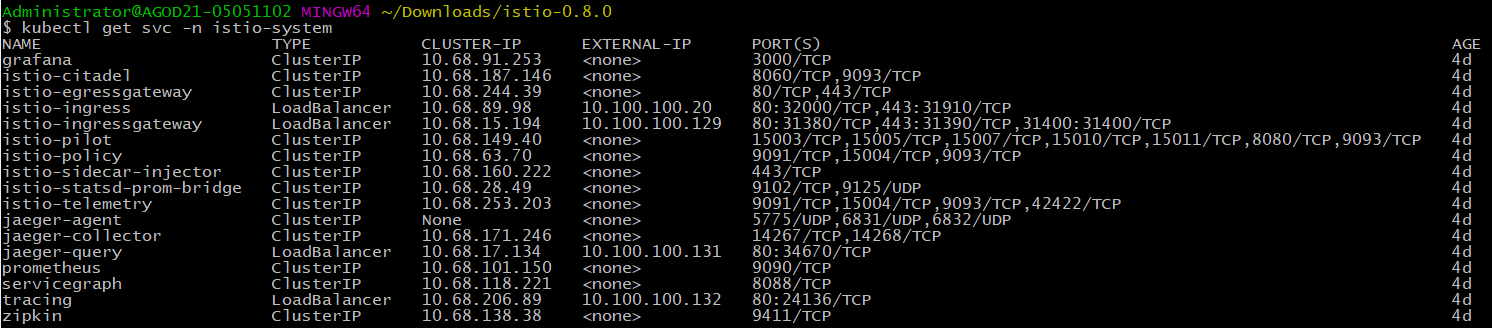
为了避免ingressgate-way所在的机子80端口被占用,特申请一台ingressgate-way的IP地址相同机子
在dns里添加了主机域名
Mesh Expansion
Istio 还支持管理非 Kubernetes 管理的应用。此时,需要在应用所在的 VM 或者物理中部署 Istio,具体步骤请参考 https://istio.io/docs/setup/kubernetes/mesh-expansion.html。
部署好后,就可以向 Istio 注册应用,如# istioctl register servicename machine-ip portname:port
istioctl -n onprem register mysql 1.2.3.4 3306
istioctl -n onprem register svc1 1.2.3.4 http:7000
Prometheus、Grafana 和 Zipkin
等所有 Pod 启动后,可以通过 NodePort、负载均衡服务的外网 IP 或者 kubectl proxy 来访问这些服务或者创建一个istio的VirtualService。apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: istio-gateway
spec:
selector:
istio: ingressgateway # use istio default controller
servers:
- port:
number: 80
name: http
protocol: HTTP
hosts:
- "prom.example.com"
- "grafana.example.com"
- "pilot.example.com"
- "zipkin.example.com"
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: grafana
spec:
hosts:
- "grafana.example.com"
gateways:
- istio-gateway
http:
- route:
- destination:
host: grafana.istio-system.svc.cluster.local
port:
number: 3000
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: prom
spec:
hosts:
- "prom.example.com"
gateways:
- istio-gateway
http:
- route:
- destination:
host: prometheus.istio-system.svc.cluster.local
port:
number: 9090
通过 http://grafana.example.com 访问 Grafana 服务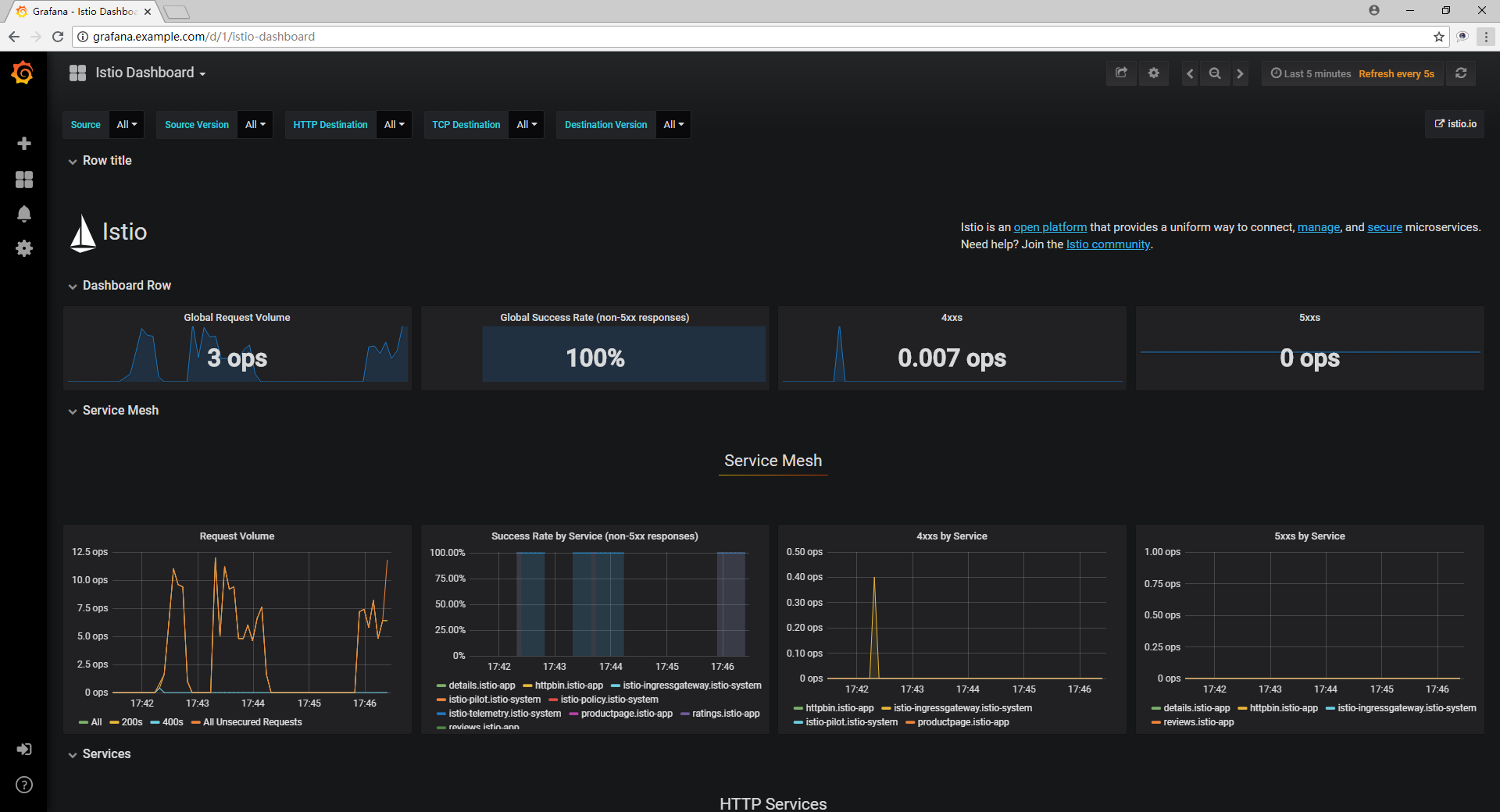
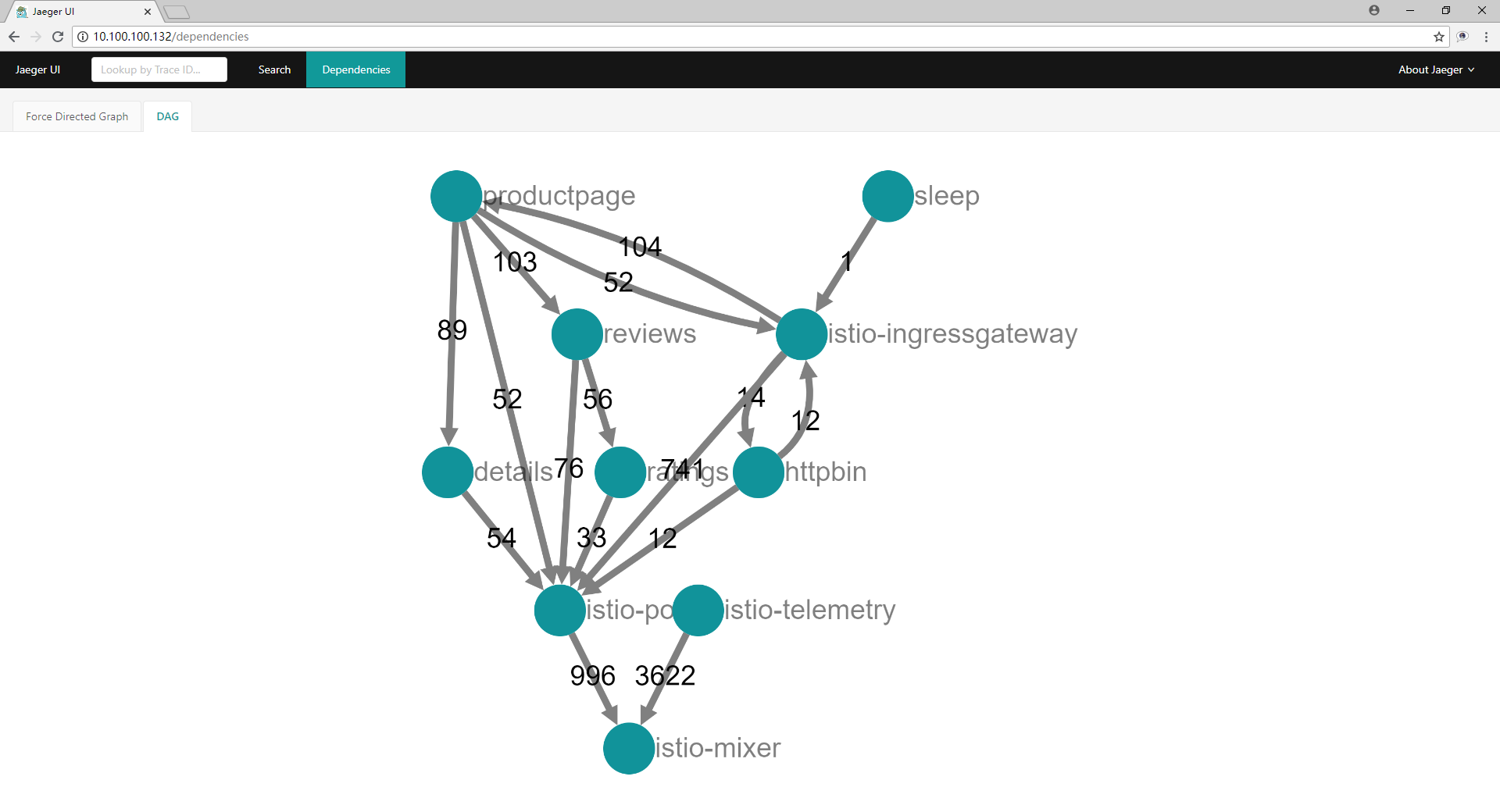
通过loabblancer访问jaeger-query,展示服务之间调用关系图